Impressive Info About How To Detect A Rogue Access Point

Pay attention to what your device list says about the new ap as it goes, and if you see an alert, make a note of what phase of adoption it was in.
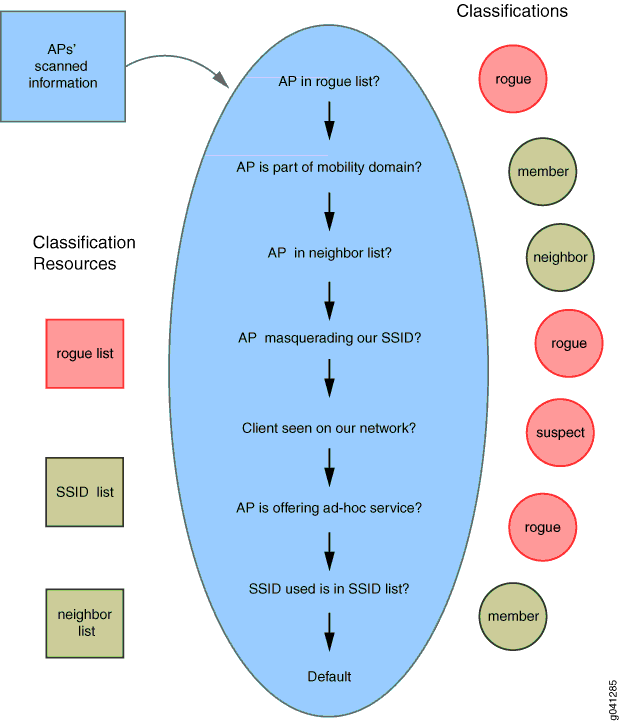
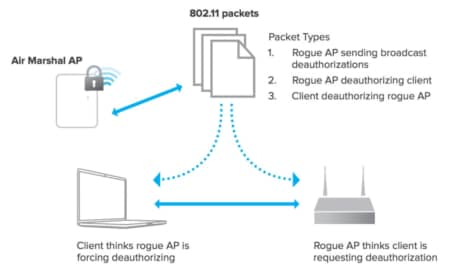
How to detect a rogue access point. Rogue access point detected will sometimes glitch and take you a long time to try different solutions. Beaconing, or requesting a beacon, and network sniffing, or looking for packets in the air. There are two basic approaches for locating rogue access points:
Those should find both an open and closed port on most. It’s difficult to determine which wireless devices to remove if you don’t have an accurate list to begin with. To clarify, under insights, click the drop down menu at the top left of the browser,.
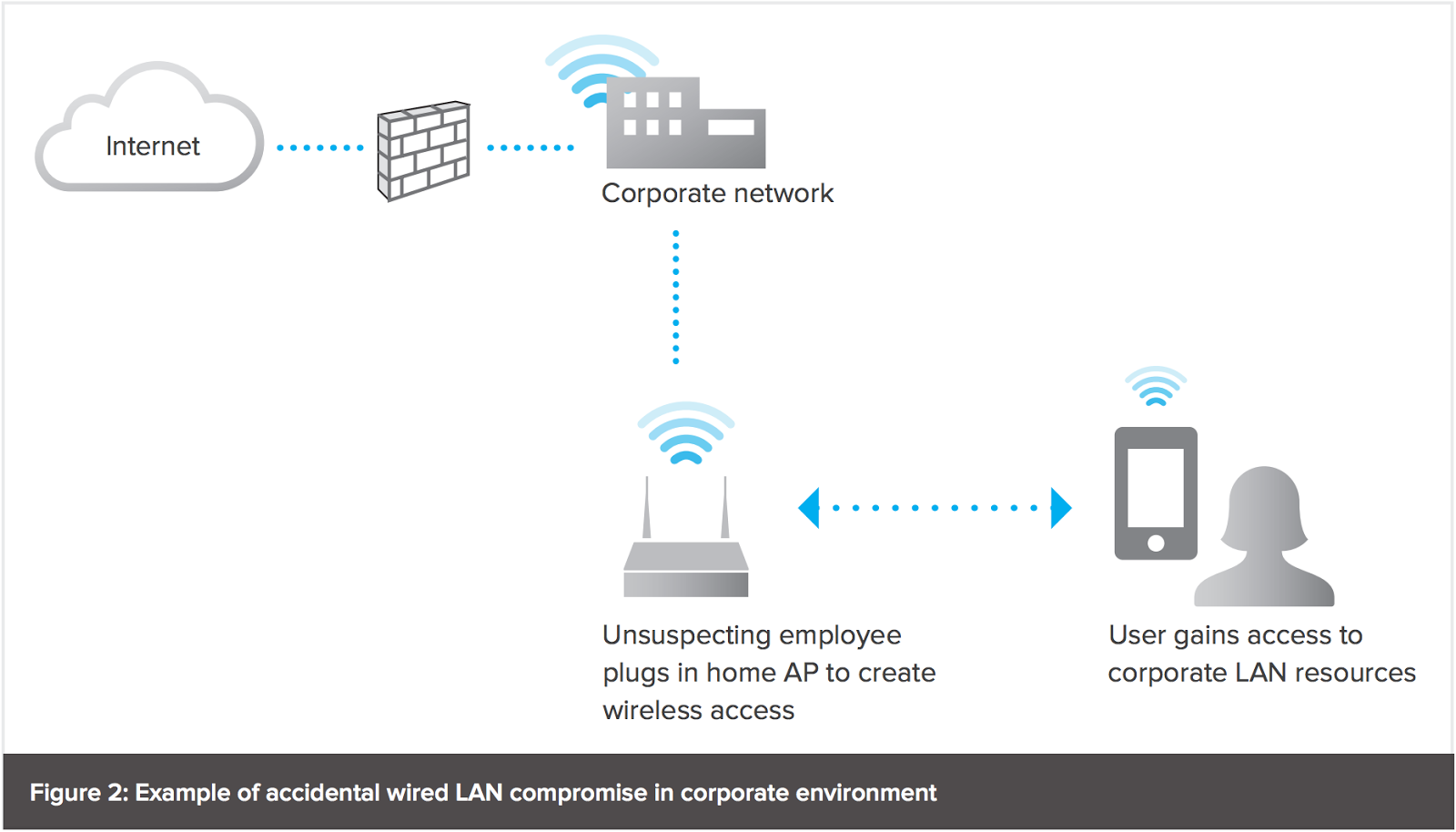
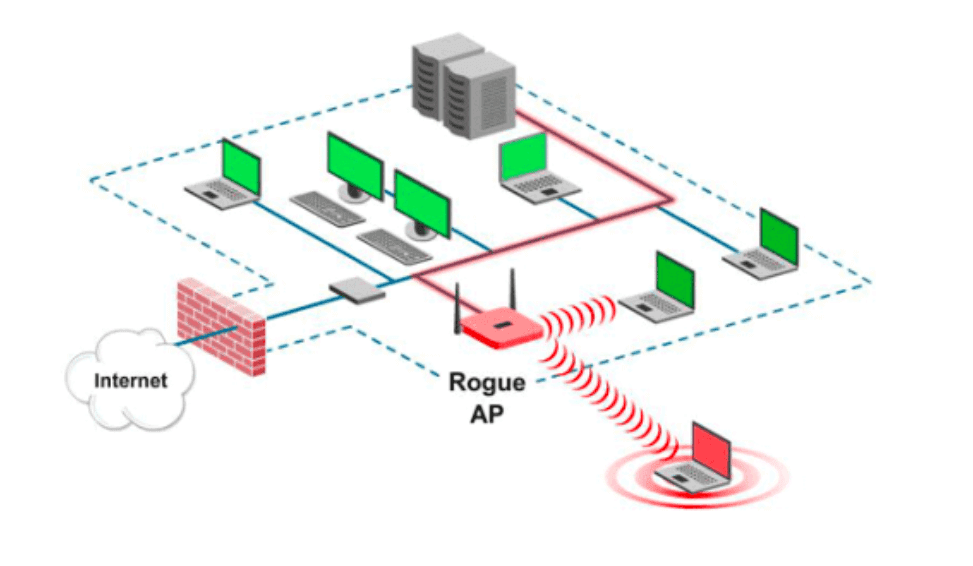
There are a couple of ways of detecting rogue aps. On top of that, the hacker can take advantage of the rogue access points to launch ddos attacks to kick you out of the network. You can configure your wireless firebox to detect rogue wireless access points that operate in the same range as your wireless network.
The authorized access points menu allows you to specify all. Check the rogue ap as known. Rogue aps can be detected by logging into your router as a system administrator.
Loginask is here to help you access rogue access point detected quickly and. To detect a rogue access point different approaches are used. Get started with pci compliance.
How to spot rogue access points a rule of thumb. Click on insights and list neighboring access points. An inexpensive but effective method for finding potential rogues is to use a freely available transmission control protocol (tcp) port scanner that identifies enabled tcp ports from.








![Pdf] A Flexible Framework For Rogue Access Point Detection | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5f7a2fec5198aa5b1f3c846b4db50aec4dff4e3b/29-Figure2.2-1.png)